Fields
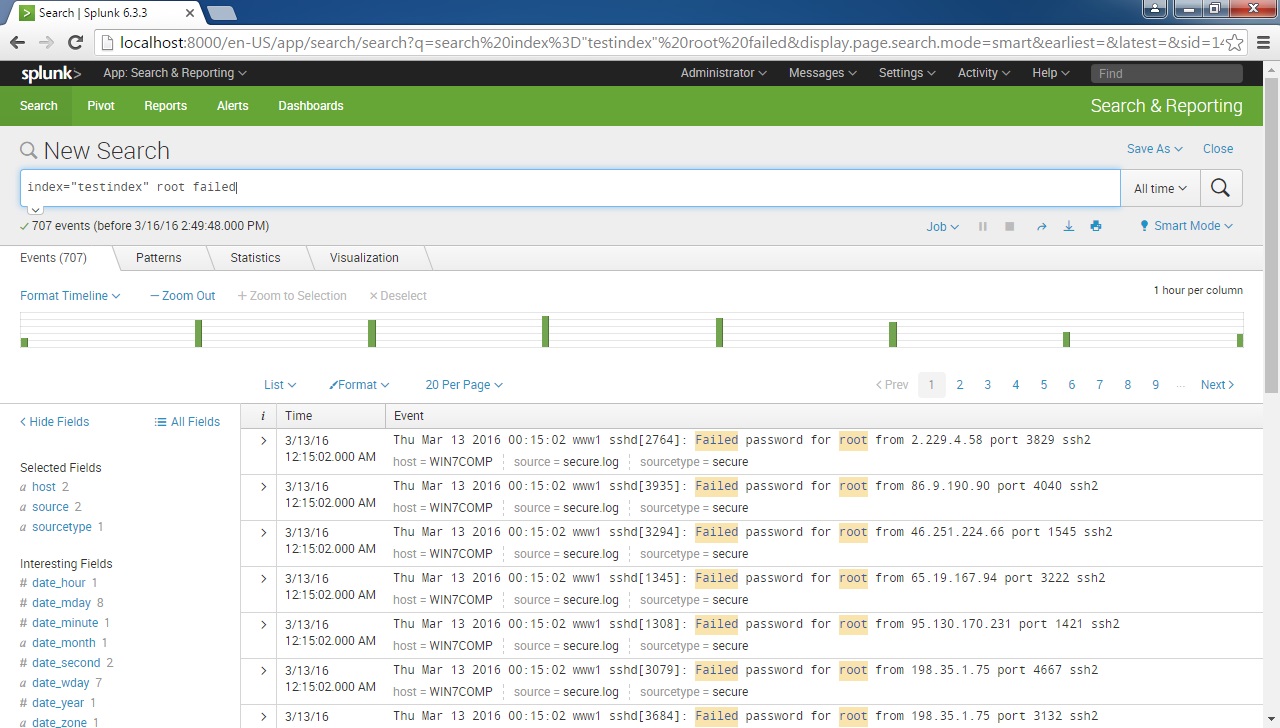
You might have noticed that, when you run a search, Splunk extracts fields from event data. The fields can be see on the left side of the Search app:
Notice that there are two kinds of fields:
- Selected fields – fields that were extracted by default. Examples of such fields include host (the host from which the event originates), source (e.g. the log file from which the event was indexed), and source type.
- Interesting fields – fields that were extracted because Splunk identified some common patterns in the data (e.g. the presence of an equal sign between a key and a value).
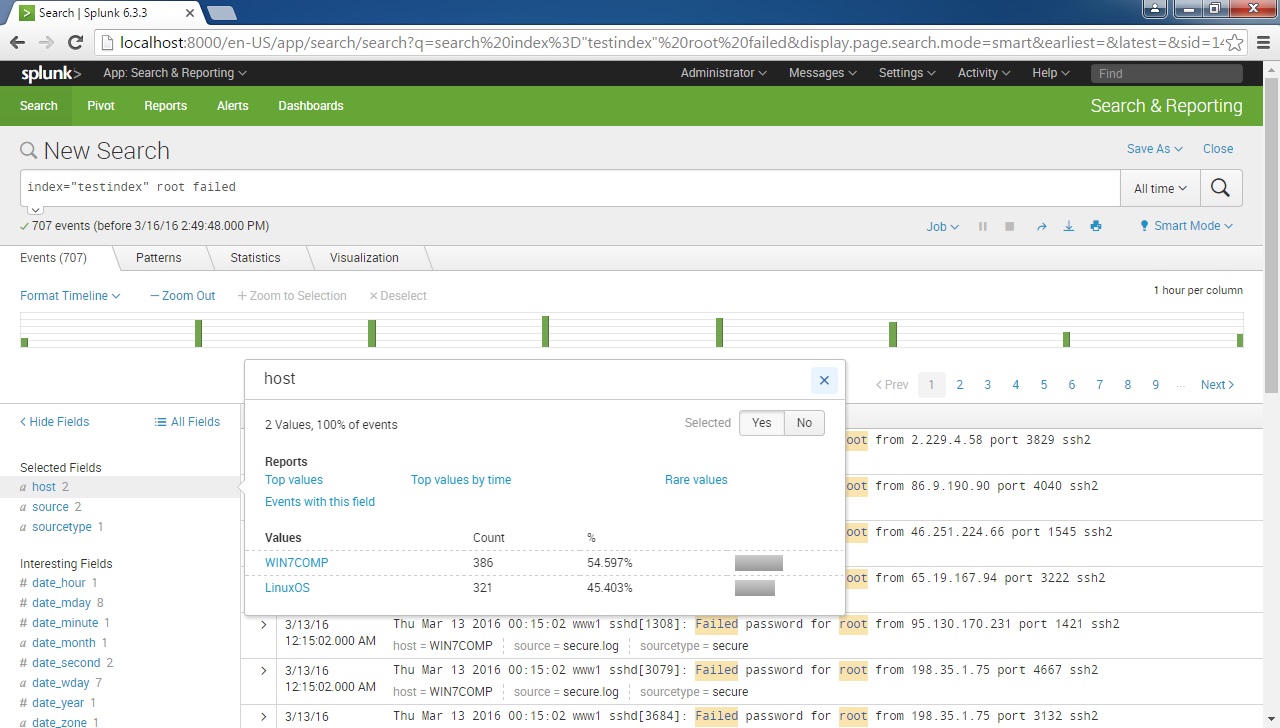
You can use these fields to narrow down your search results. For example, we can click on the Host field to display the hosts from which the events originate:
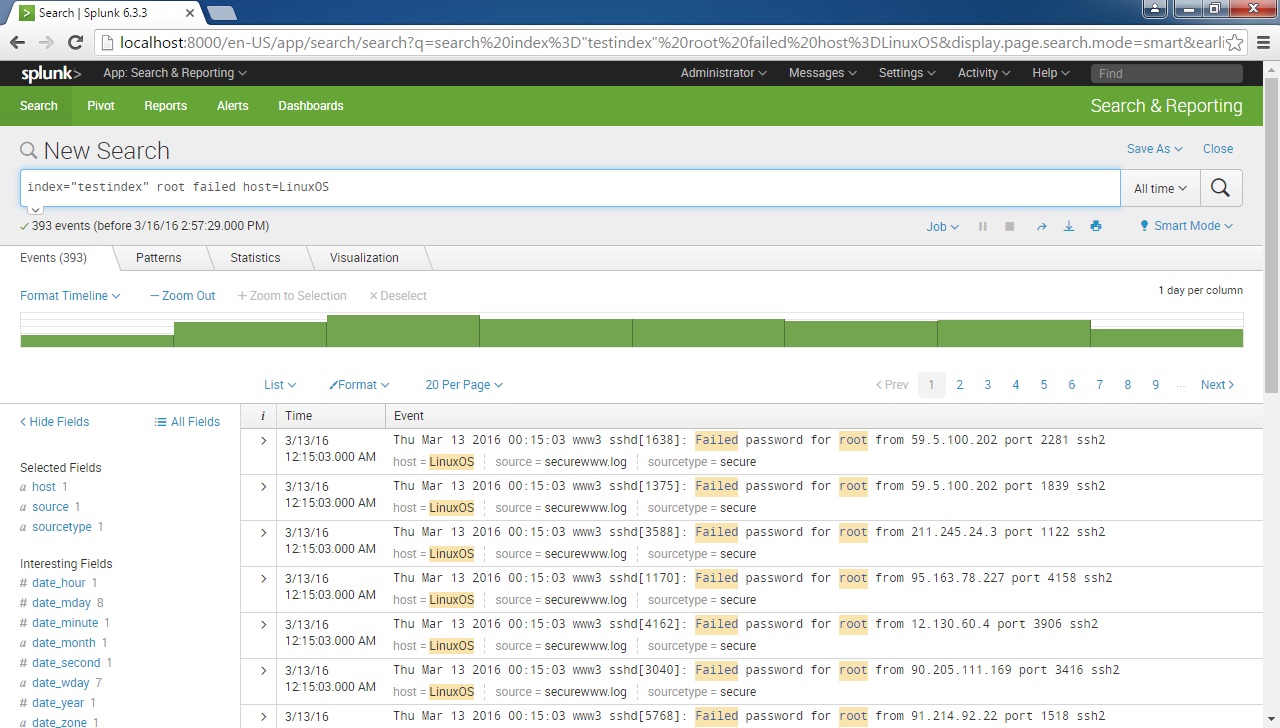
We can then click on the hostname listed. This will add the host field to the search expression, which means that only events from originating from that host will be displayed: