A short introduction to… Physical access control system (PACS)

Physical access control system (PACS) is a type of physical security system typically used by businesses, military sites, or even private apartments to control access to a certain area or building. It is designed to grant access to employees or guests who work at a site by electronically authenticating their credentials.
Some of the benefits of using an access control systems include:
- easy way to limit access to a certain physical location (e.g. a server room or a warehouse)
- higher level of accountability, security, and flexibility
- transaction reports when somebody came in our left
- stolen or lost card can be quickly disabled, unlike with real keys
An access control system consists of the following components:
Access control controller
The controller is the center of physical access control systems connecting software, readers, and locks. It receives the credentials from the reader and verifies if the credential is valid. If it is, the command is sent to the access point and the doors are unlocked. If the credentials are not valid, the door will stay locked.
Controllers are usually connected to a PC running access control software (the brain of the system). They usually have built in memory that enables them to run even if the communication with the software is interrupted.
Controllers typically handle up to 8 doors. They can be configured with a list of valid times the users can open the door. Also, the doors can be configured to be automatically unlocked or locked.
Readers
Readers are stationed at the door they are controlling and are used to authenticate the user. The user can authenticate via an RFID card, PIN, or even a fingerprint. The reader sends this data to the controller which verifies whether the credential is valid.
RFID readers operate at two frequencies:
- 125 kHz – an older format that is still sometimes used, however it should be avoided because of the low security it offers.
- 13,56 MHz – a newer format that offers two way communication between reader and card. It allows for higher security since its communication is encrypted.
Locks
Locks represents the physical security barrier. Electromagnetic locks and electric strikes are most often found in an access control system. Locks are mounted on the door or door casing and connected to the controller.
Software
Most access control system manufacturers have developed a specialized software that is used to manage the system – credentials management, door management, reporting… The software represents the brain of the system and usually supports multiple users with different permissions. However, the software is sometimes not used in smaller installations to reduce costs.
Access control system operation
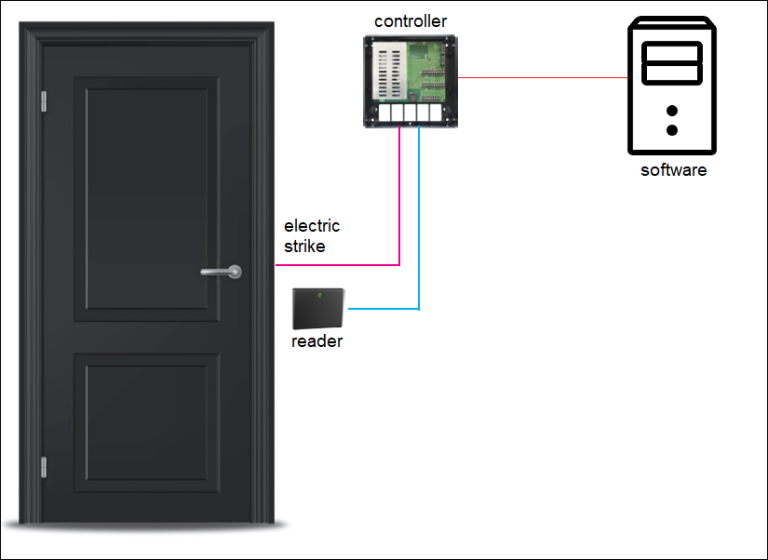
Consider the following simple access control system:
As you can see from the picture above, the reader is stationed at the access point. The door is controlled by an electric strike. Once the user presents its credentials to the reader the data is sent to the controller which determines whether the credential is valid. If it is, the signal will be sent to the electric strike and the door will open.