Collect event logs from a local Windows machine
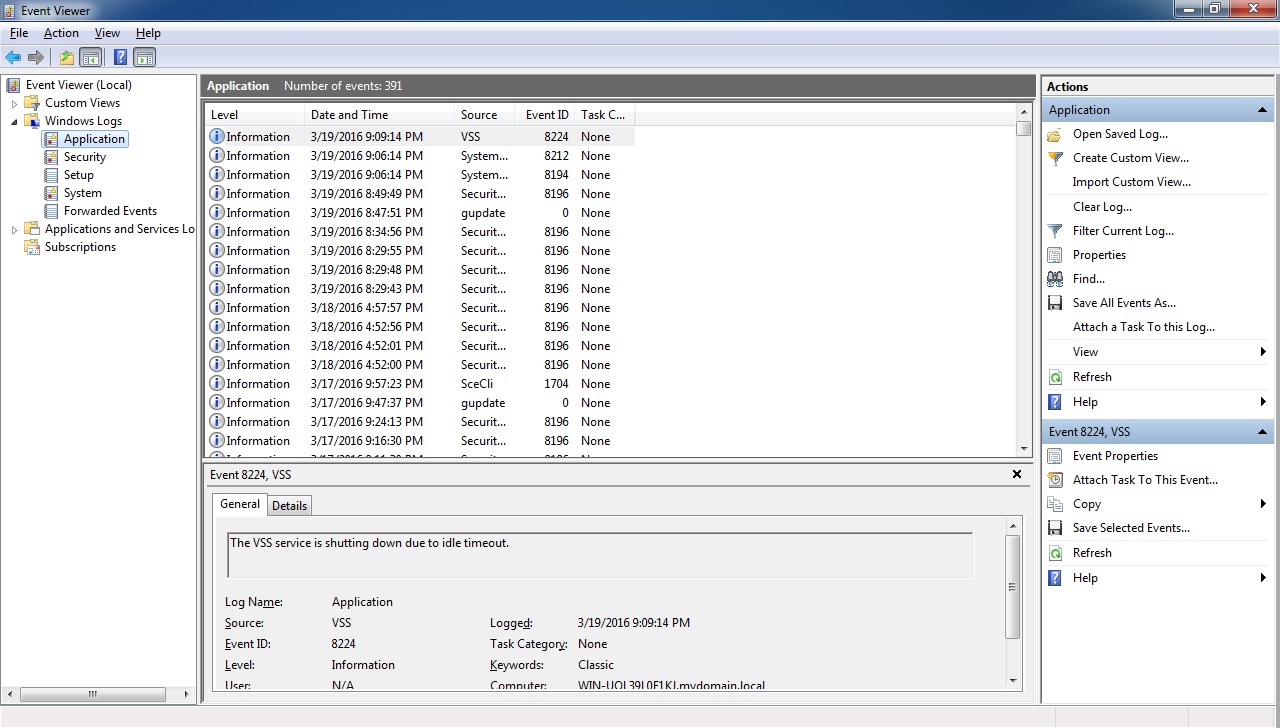
You probably know that Windows record significant events on your computer (such as when a user logs on or when a program encounters an error). These logs are maintained by the Event Log Service and can be displayed using Event Viewer:
Splunk can monitor and collect logs generated by the Windows Event Log Service on a local or remote Windows machine. In this section we will describe how you can monitor Windows logs on a local Windows machine where Splunk is installed.
Here are the steps to configure event log monitoring on a local machine:
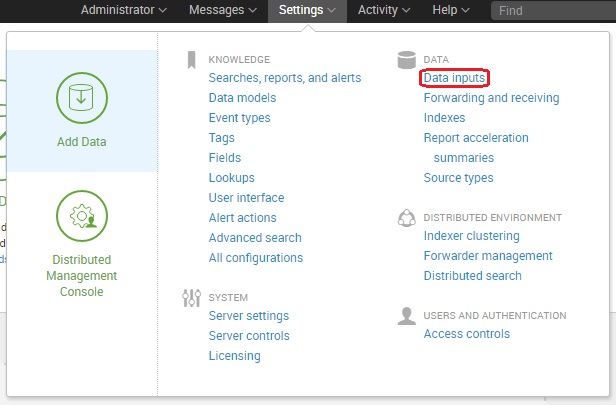
Go to Settings > Data inputs:
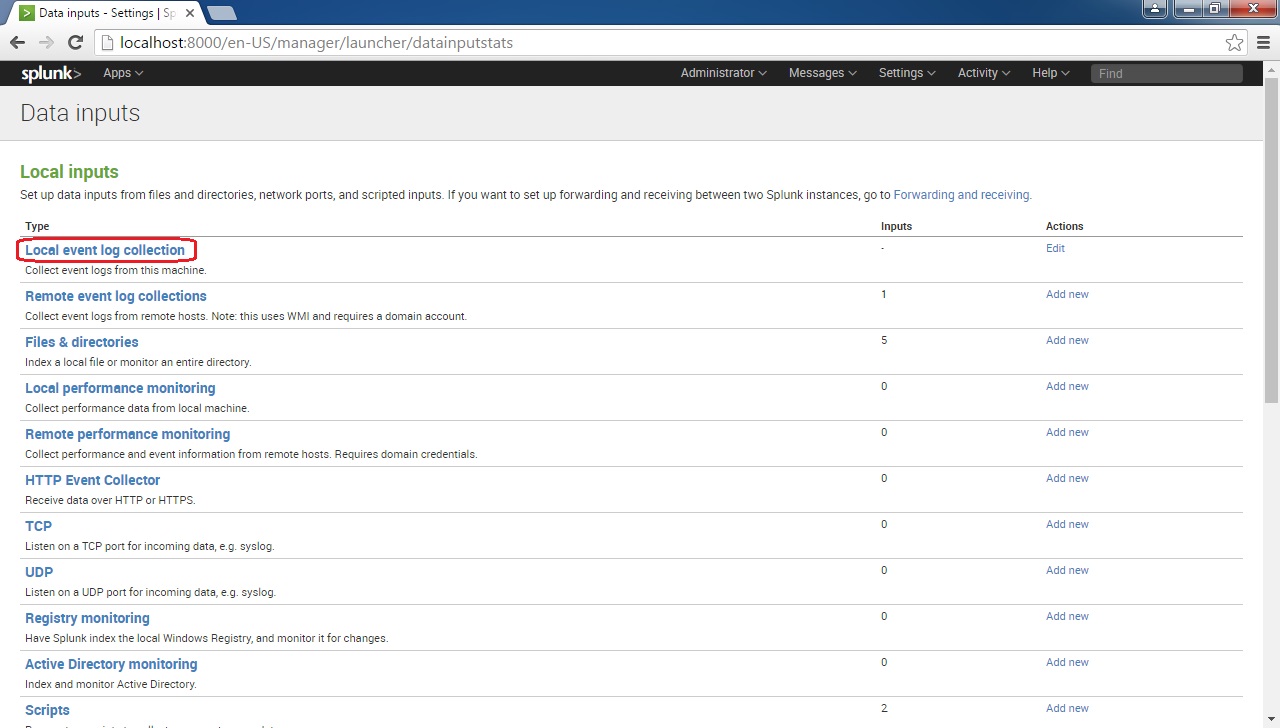
Click Local event log collection:
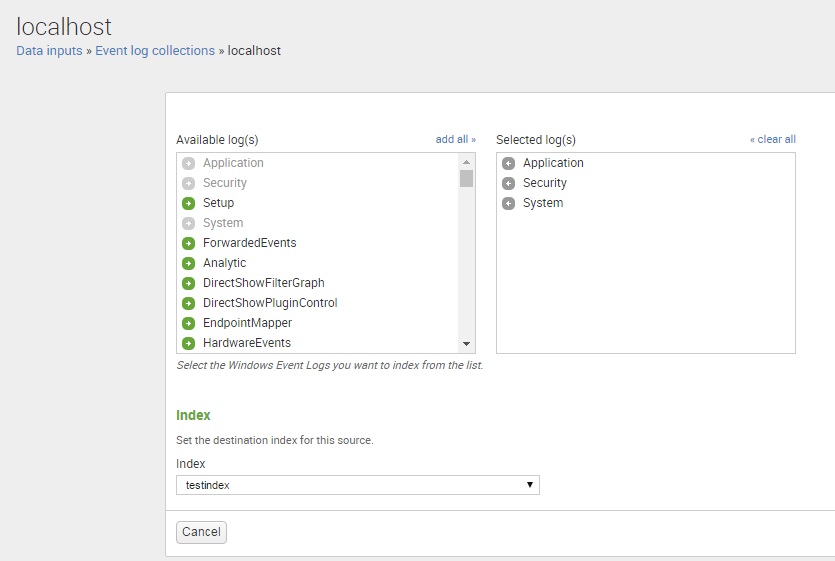
In the Available log(s) list box, choose the Event Log channels you want this input to monitor. We have selected Application, Security and System logs. You also need to choose the index that will store the data:
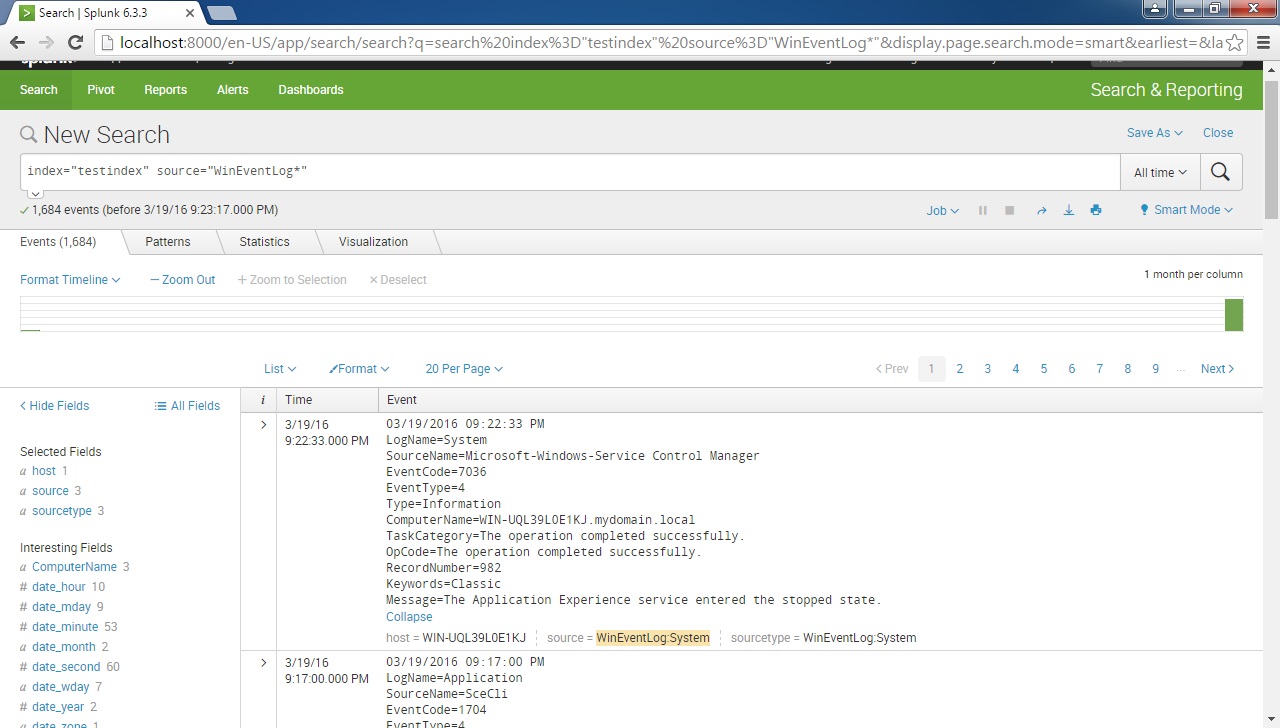
And that’s it! We can now search the Event logs from the local machine: