Collect Windows host information
Splunk enables you to collect detailed statistics about the local and remote Windows machines. You can collect information such as the computer hostname, the operating system version and build numbers, the CPU installed on the system, disk space, installed services, running processes…
Here is how you can collect information about a local Windows machine:
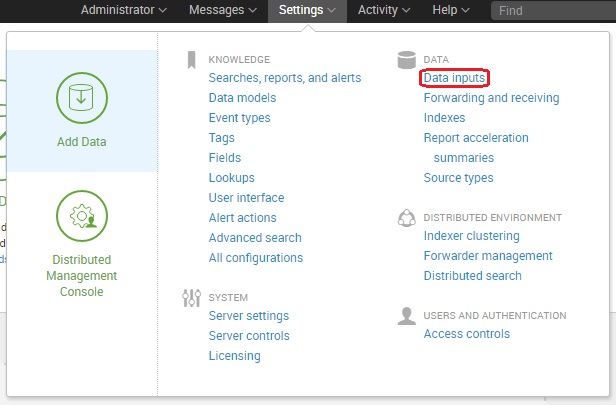
Go to Settings > Data inputs:
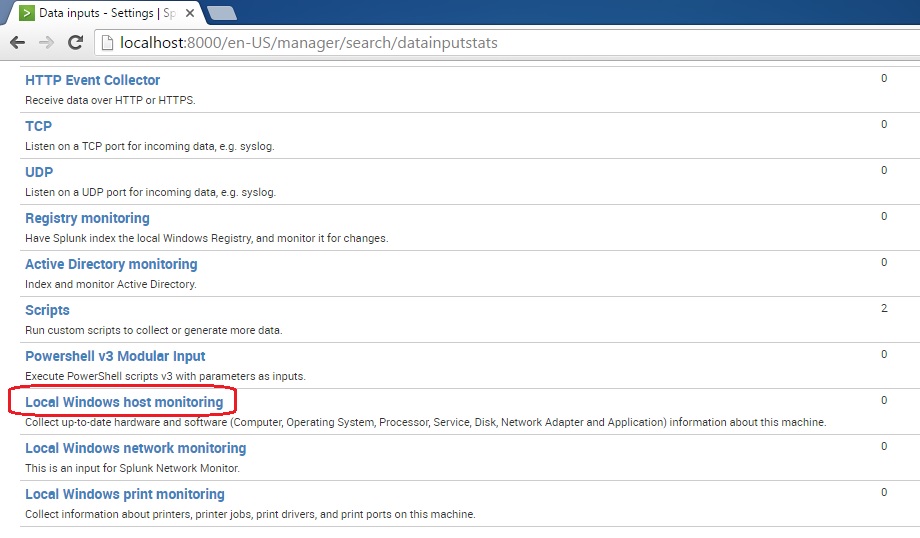
Click Local Windows host monitoring:
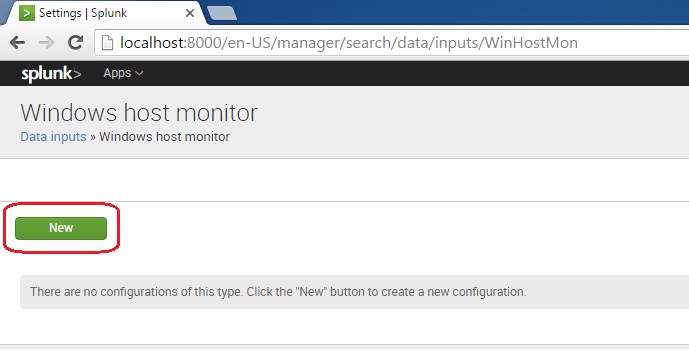
Click New to add an input:
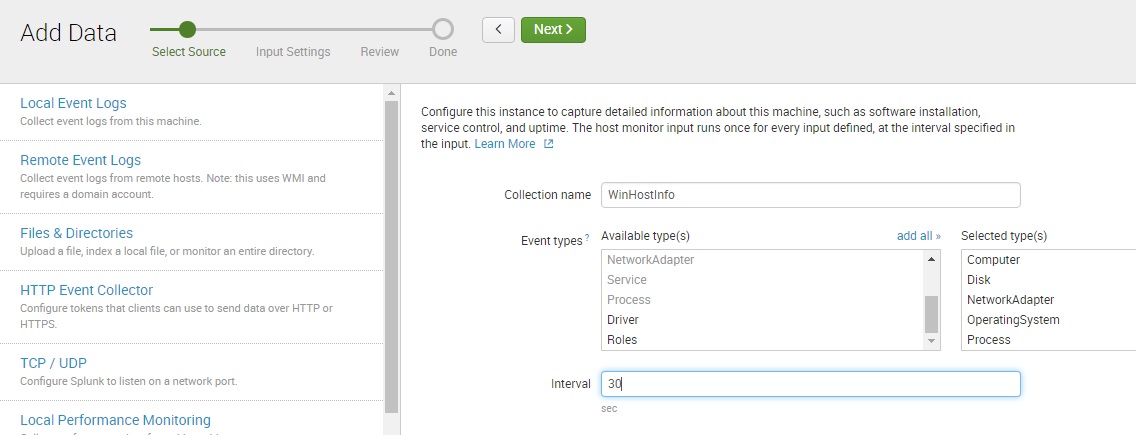
In the Collection name field, enter the name for this input. In the Event types list box, select the host monitoring event types you would like to monitor. In the Interval field, enter the time, in seconds, between polling attempts for the input:
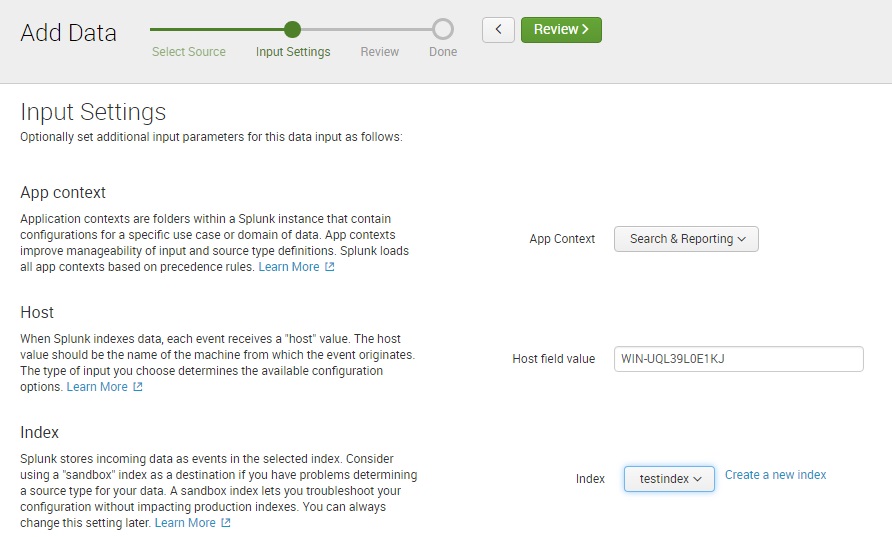
Next, you can select the App Context for this input, the host name value, and the index in which the data will be stored:
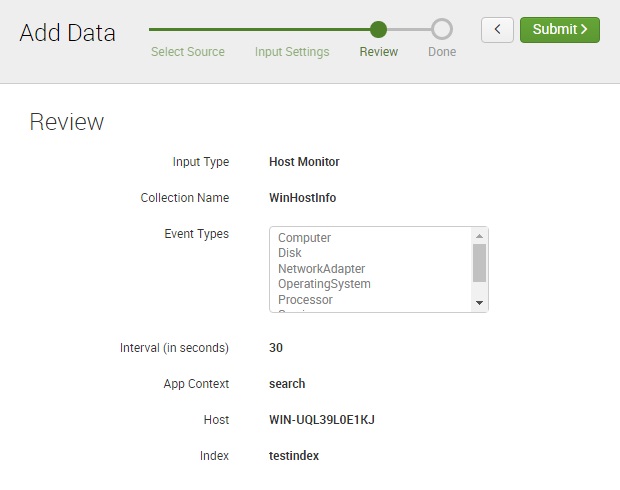
Review the information and click Submit:
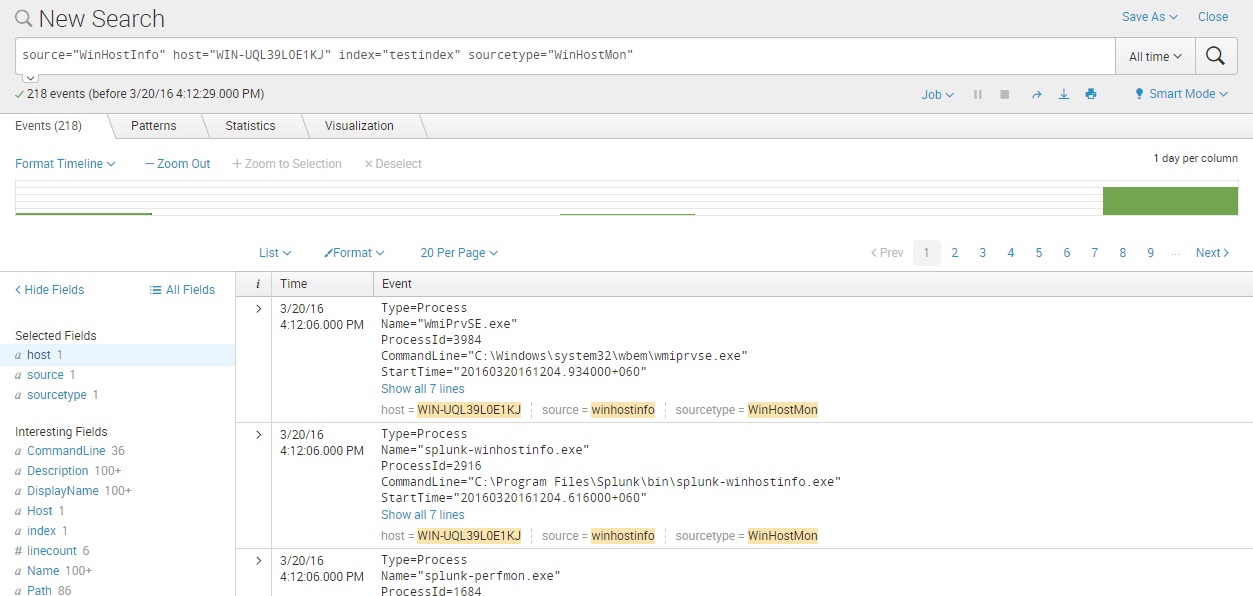
And that’s it! We can now search the host information we’ve collected: