Boolean expressions
Three types of Boolean operators available in Splunk:
- AND – implied between terms, so you do not need to write it.
- OR – used to specify that either one of two or more arguments should be true.
- NOT – used to filter out events containing a specific word.
The Boolean operators listed above must be capitalized (or Splunk will not evaluate them as an operator).
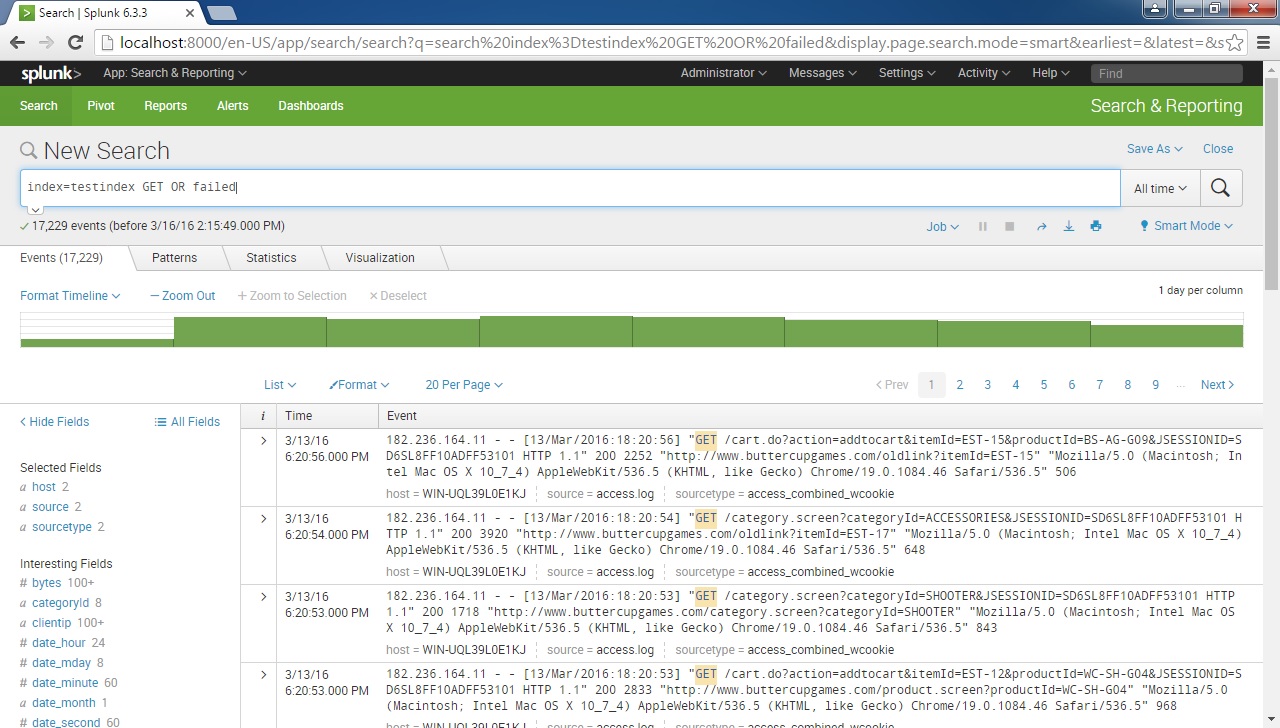
For example, to search for all events that contain either the word GET or the word failed, we would use the following search expression:
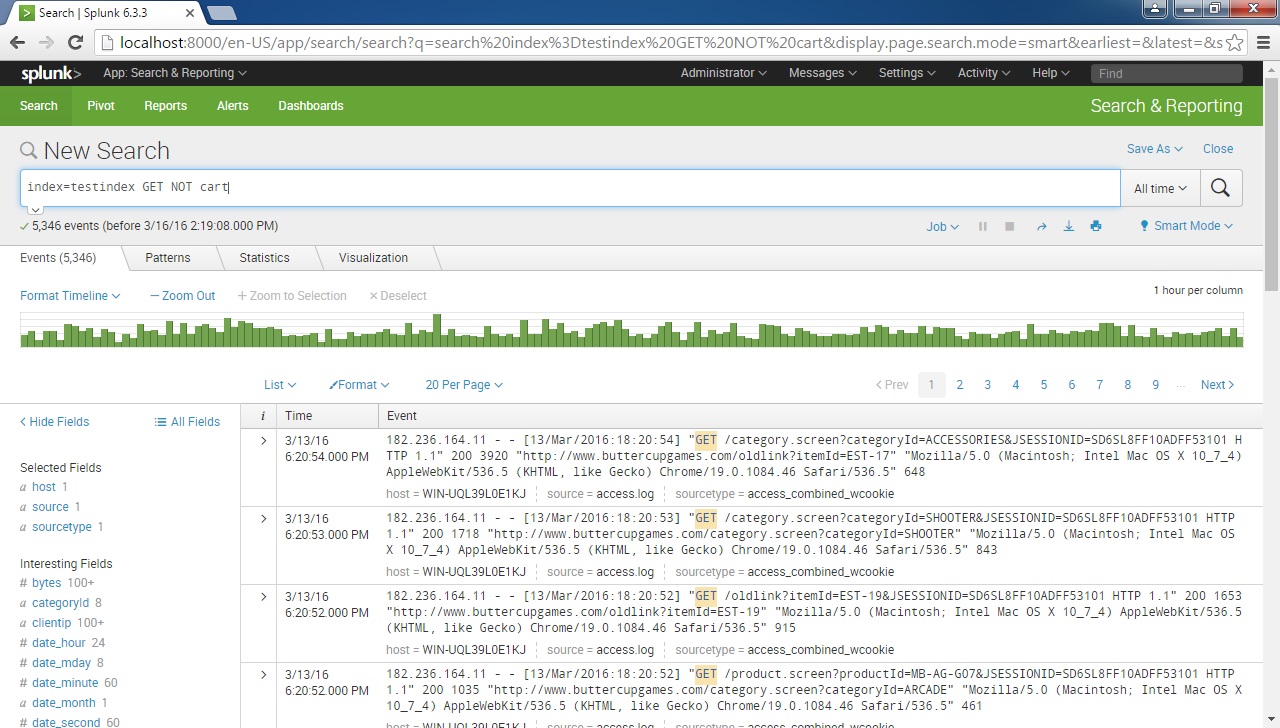
To search for all events that contain the word GET but don’t contain the word cart, we would use the following search expression:
It is recommended to use parentheses to group terms. When evaluating Boolean expressions, the precedence is given to terms inside the parentheses.