Example search
Now that we’ve added data to Splunk and learned the basic rules for searching, we can finally begin to search our events. To search your indexed data, simply type the search term in the Search bar and press enter. Although not required, it is recommended to specify the index you would like to search, as this will ensure a more precise and faster search:
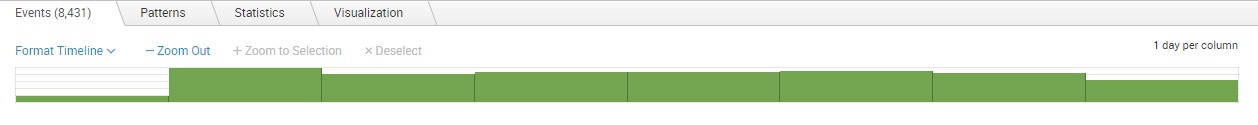
As you can see from the picture above, we’ve searched for the keyword GET in the index called testindex. Splunk found 8,431 events that contain the word GET. Here is the overview of the components in the dashboard:
Timeline – a visual representation of the number of events matching your search over time:
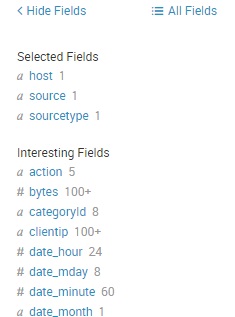
Fields – relevant fields extracted by Splunk. You can use these fields to narrow down your search results:
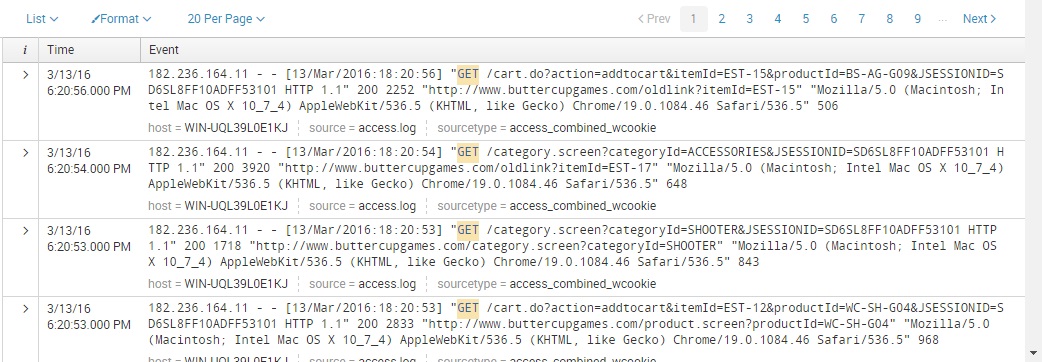
Results – the events that matches your search. Events are ordered by Timestamp, which appears to the left of each event: