Add data to Splunk
There are three ways to add data to Splunk:
- Upload – you can upload a file or archive of files into Splunk Enterprise for indexing. Note that Splunk consumes the uploaded file(s) only once and it does not monitor it continuously.
- Monitor – you can use this option to monitor files, directories, network streams, scripts, and other type of machine data that Splunk can index. This is the option you would most likely use for your production environment.
- Forward – you can use this option to receive data from forwarders.
The easiest way to add data to Splunk is to use the first option (Upload). Here is how we would upload a file to Splunk:
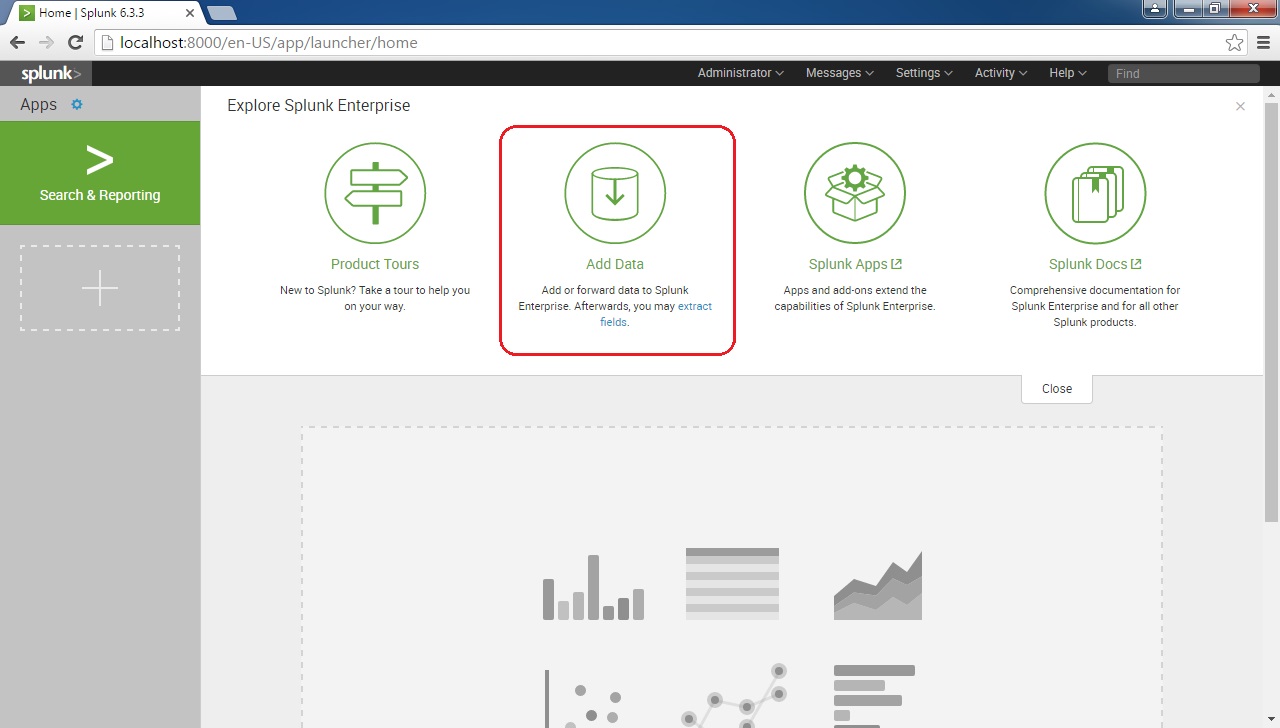
From the home screen, click on the Add Data icon:
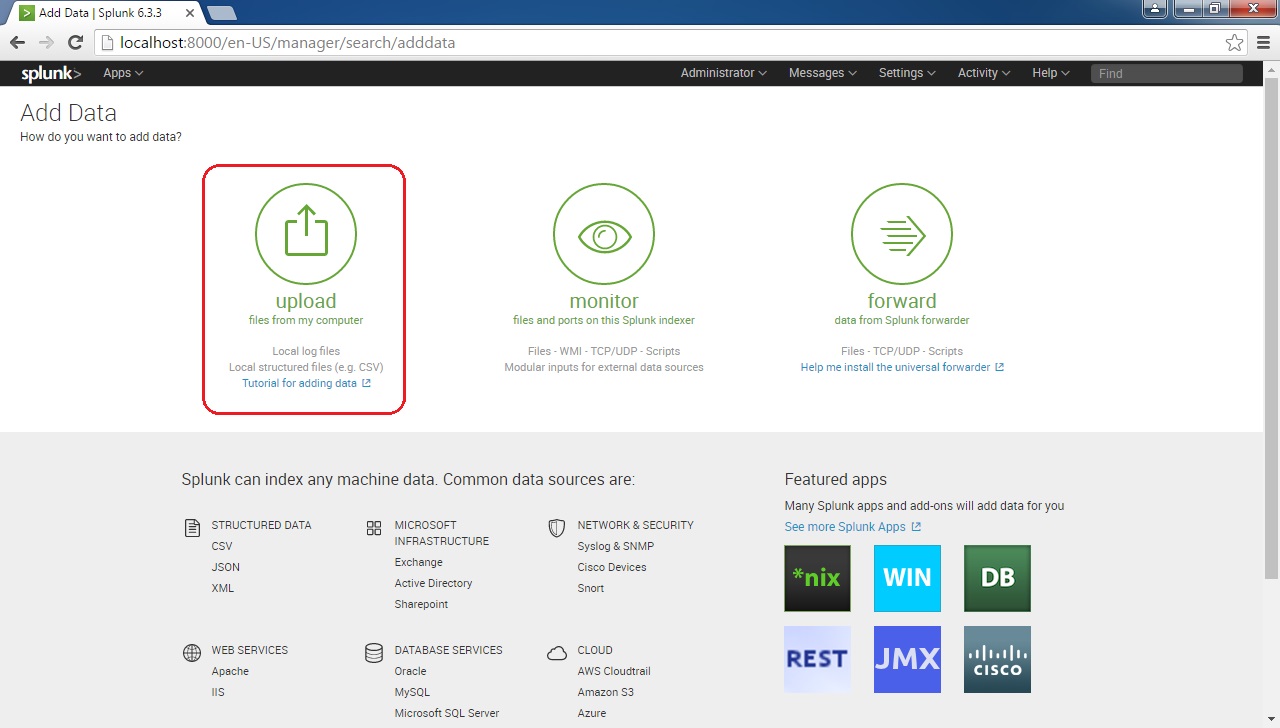
Click on the Upload icon:
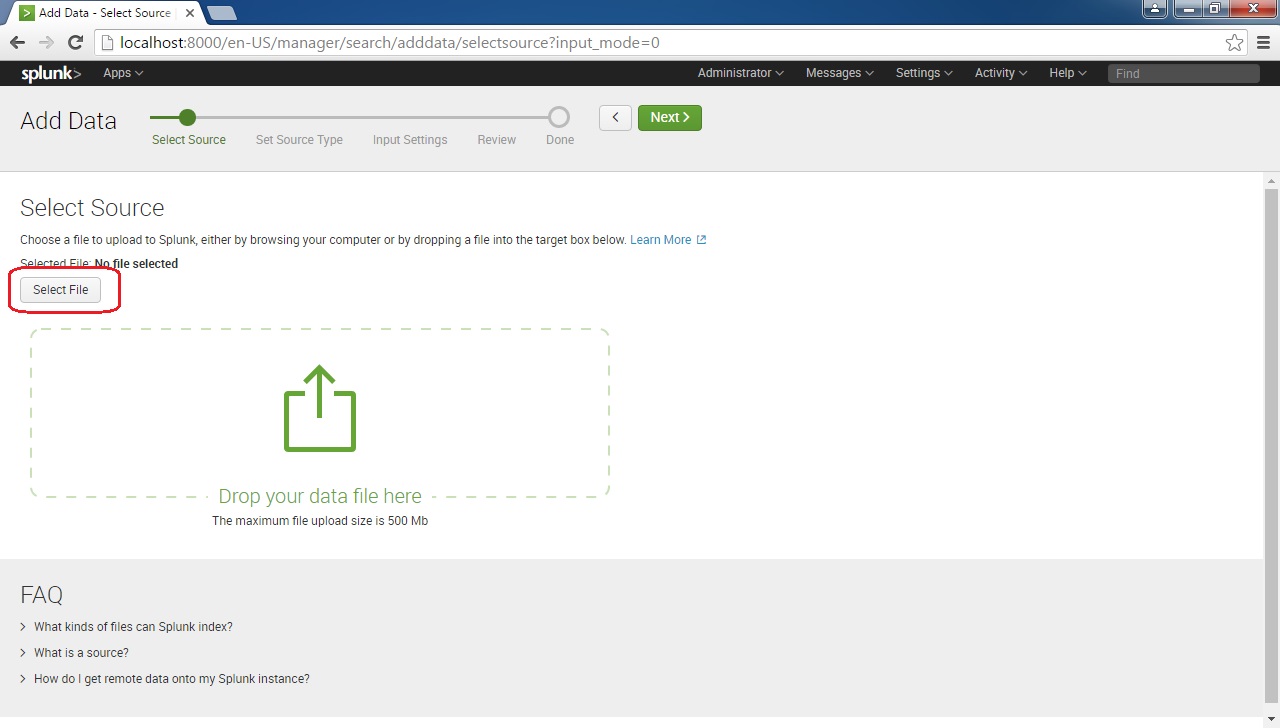
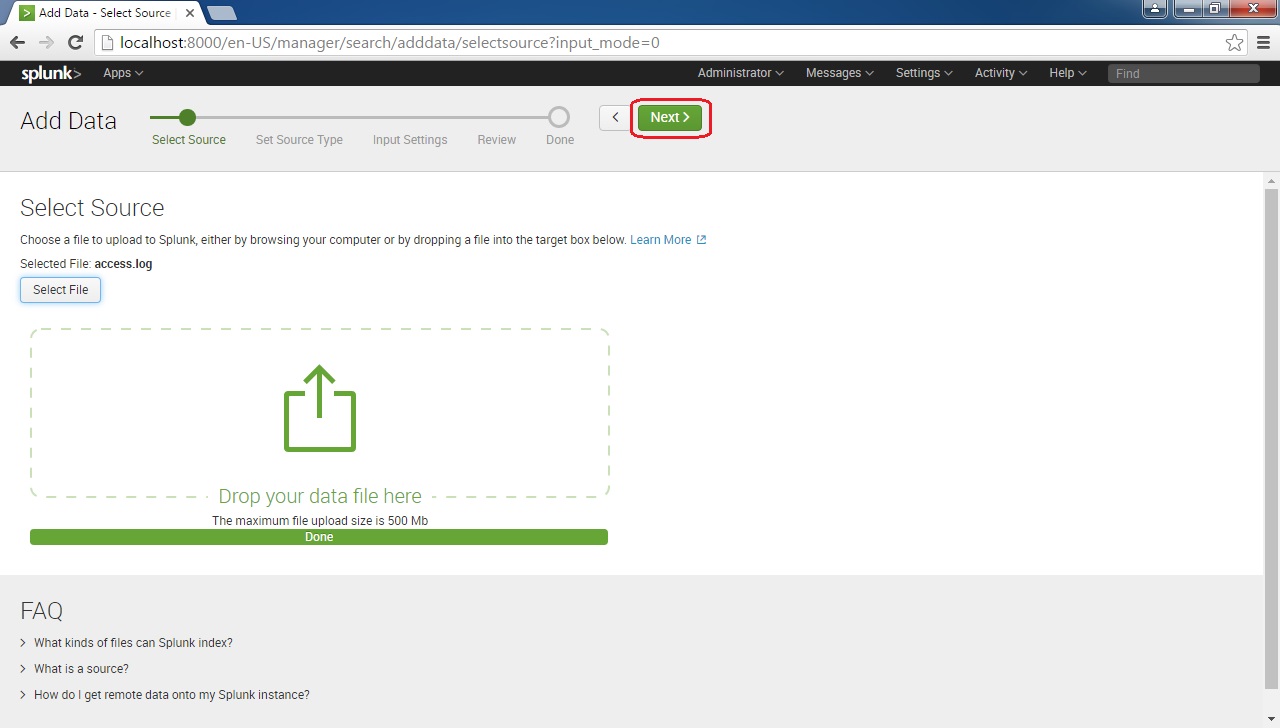
Next, you will need to select the file source. To do this, click on the Select File button:
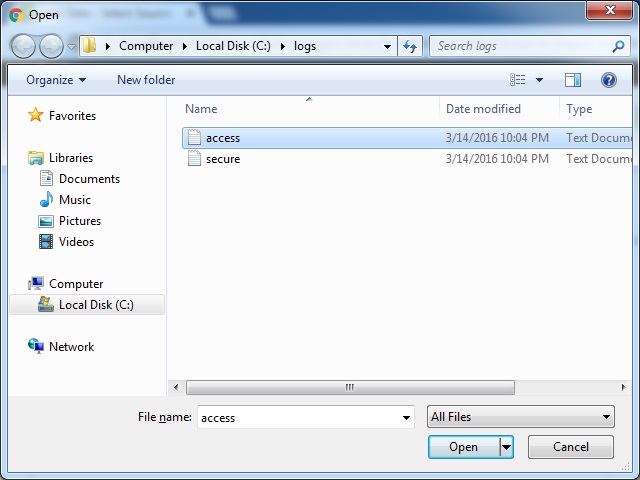
Browse to the file you would like to include:
After the file upload finishes, click the Next button:
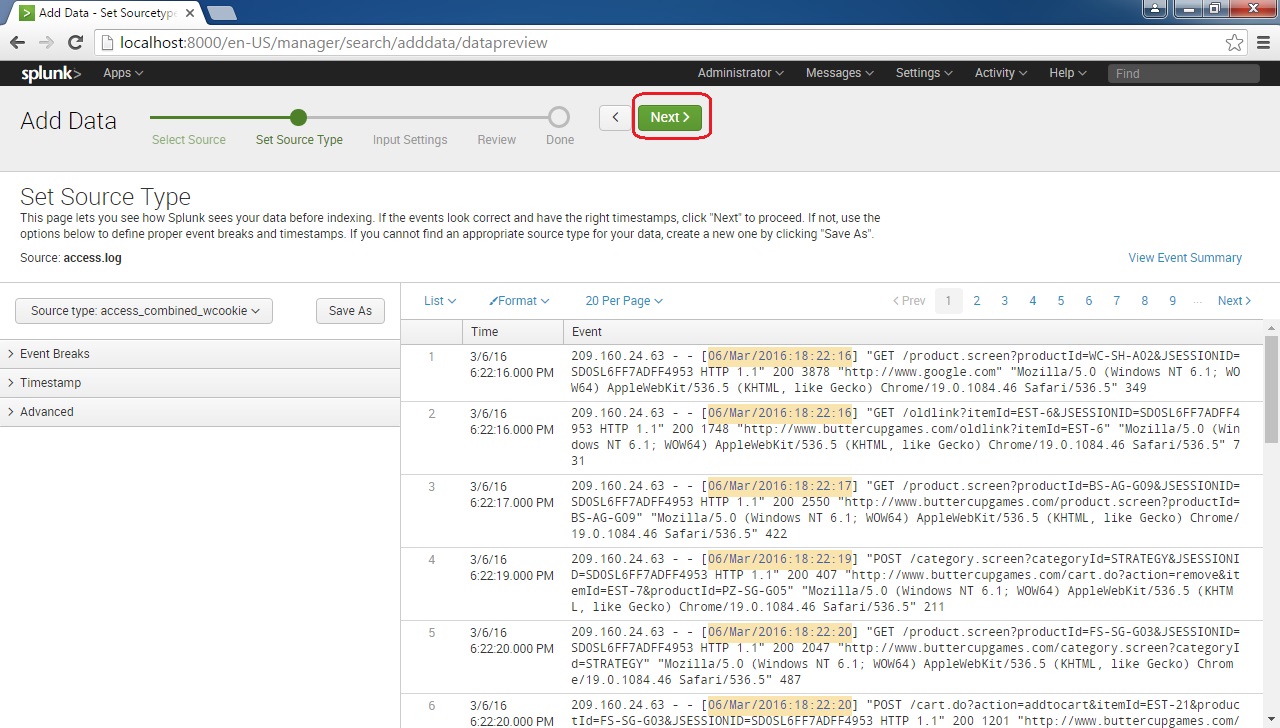
You should get the Set Source Type page, where you can make adjustments to how Splunk indexes your data. This page allows you to preview how Splunk will index your data. One of the options you can adjust is the source type. This field determines how Splunk will format the data during indexing. Splunk comes with a large number of predefined source types and attempts to assign the correct source type to your data based on its format.
If you are not satisfied with the default source type that was assigned by Splunk, you can choose other source types or use other options (Event Breaks, Timestamp, and Advanced) to manually adjust how Splunk will format data. In our case, Splunk has formatted the data correctly so we will press Next:
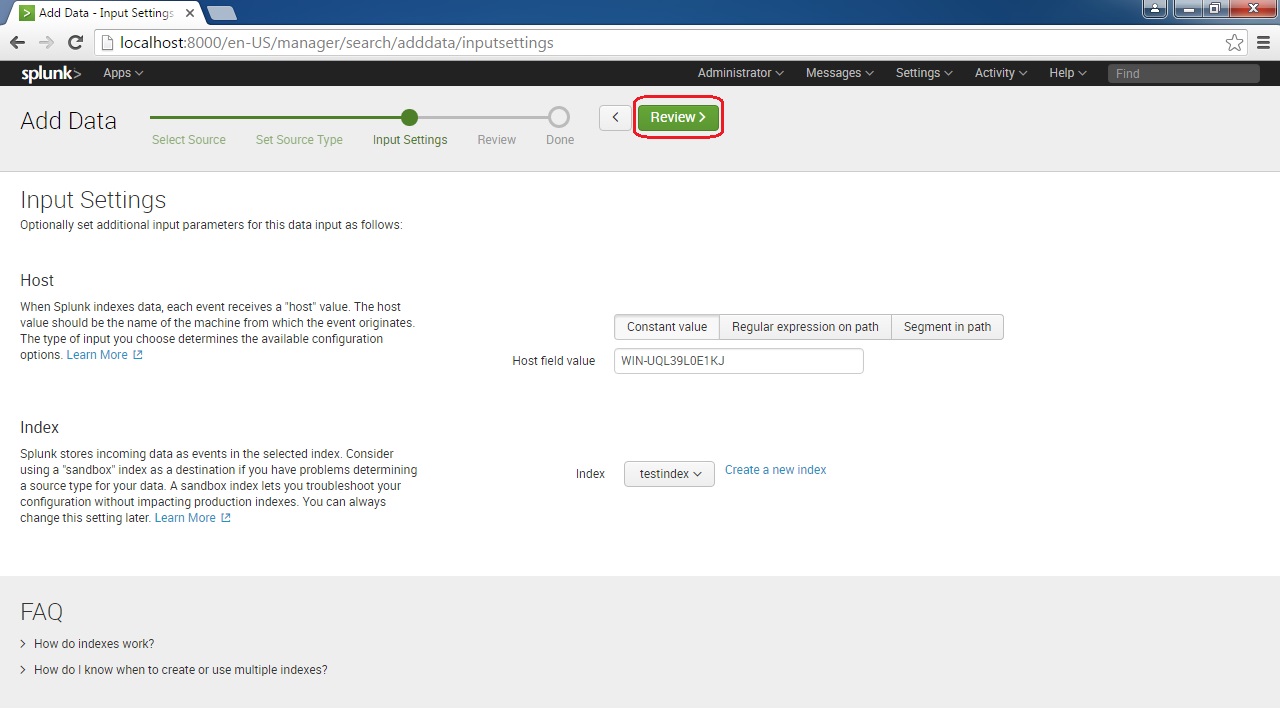
Next, we can configure Input Settings. We can configure the hostname (or IP address) of the host from which the log originates. We can also choose the index in which we would like to store the events. Select your options and click the Review button:
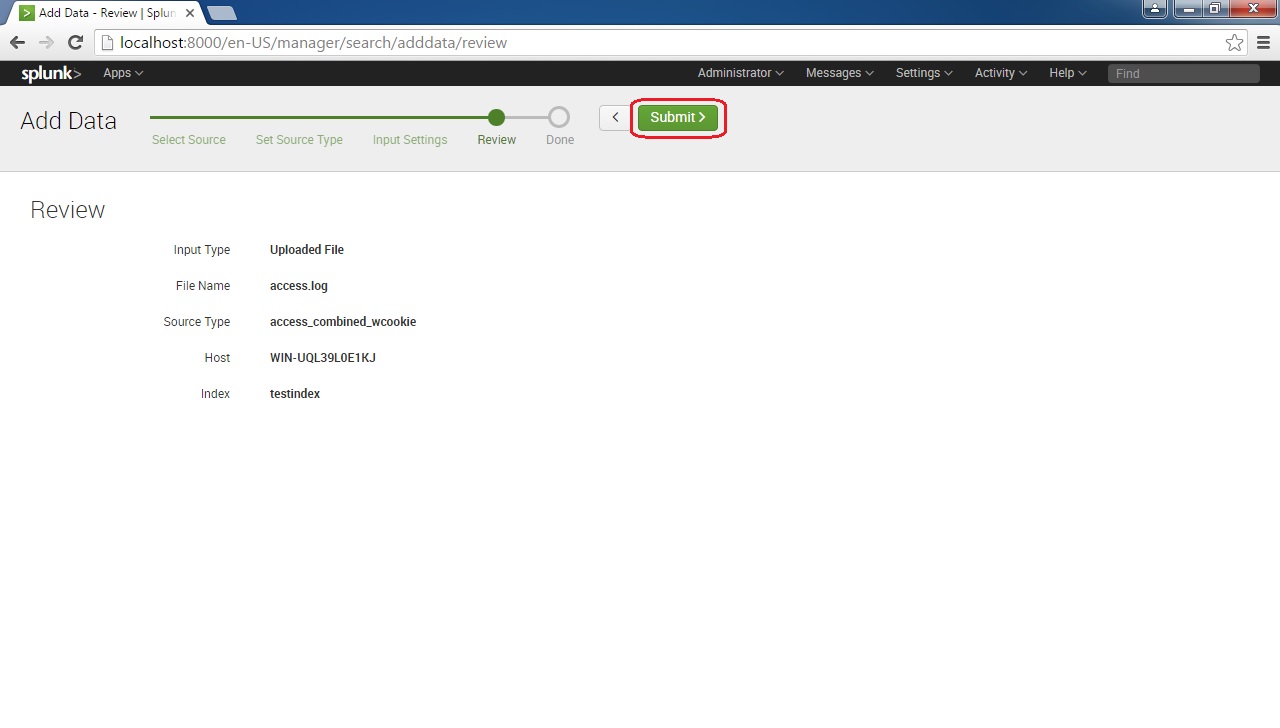
Review the settings and click Submit to finish the process:
And that’s it! You can verify that the data was added successfully by clicking on the Start Searching button: