The sip.conf file
SIP channels in Asterisk are configured in the sip.conf file. Since SIP (Session Initiation Protocol) is so widely used, the corresponding SIP module in Asterisk offers many features and options.
Because of the popularity of SIP, almost all of the examples in this course will use this protocol. To begin with the SIP configuration, create the SIP configuration file in the /etc/asterisk directory:
touch /etc/asterisk/sip.conf
Configuration files for all channel modules have a section called [general] that appears at the top. This section contains general configuration options for how the protocol relates to your system, and can also used to define the default parameters. Enter the following lines into the newly created sip.conf file:
[general] context=public ; default context allowguest=no udpbindaddr=0.0.0.0 tcpenable=no
Here is a brief description of each line:
- [general] – starts the general section.
- context=public – specifies the context for all unauthenticated calls.
- allowguest=no – disables unauthenticated guest calls.
- udpbindaddr=0.0.0.0 – specifies the IP address to bind UDP listen socket to (0.0.0.0 means bind to all IP addresses on the system).
- tcpenable=no – tells Asterisk to not support TCP.
Now we can configure our SIP peers (devices). For a start, we will configure two devices. Enter the following lines below the general section:
[bob] type=friend context=local allow=ulaw,alaw secret=verysecret1 host=dynamic [alice] type=friend context=local allow=ulaw,alaw secret=verysecret1 host=dynamic
We’ve defined two peers – bob and alice. Here is a description of the options specified for each peer:
- type=friend – this option determines how Asterisk interprets incoming SIP requests. The value of friend is most commonly used with SIP telephones and it forces Asterisk to match incoming requests to a configuration entry using the username in the From header of the SIP request or using the source IP address and port number.
- context=local – specifies that the requested extension number will be handled by the dialplan in the context defined in the device configuration; in our case, the context called local. In other words, this options determines how the channel enters the dialplan.
- allow=ulaw,alaw – specifies the audio codecs that are accepted from and are offered to the telephone. I’ve defined two codes which are supported by most VoIP providers: ulaw and alaw.
- secret=verysecret1 – a shared secret that SIP telephone needs to use to login to Asterisk.
- host=dynamic – defines the IP address of the SIP telephone. The value of dynamic specifies that the telephone will tell Asterisk where it is on the network. You could also specify a static IP address for your SIP phone.
If you specify an option multiple times, for example inside the general section and in the specific section for the device, Asterisk will assign the option in the following order:
- the specific section for the device (e.g. [bob])
- the template for the section (we’ll explain templates in the next section)
- the [general] section
- the hardcoded defaults
In other words, if we define different values for an option in both the specific section for the device and the general section, Asterisk will use the value defined in the device section.
Every time you update sip.conf, you will need to apply the new SIP configuration. This is done is from the Asterisk CLI, so you need to start it using the asterisk -rvvv command. The -r option specifies that we want to connect to a running Asterisk process, while the vvv flags increase the verbosity in the console:
asterisk -rvvv
If you get the Unable to connect to remote asterisk (does /var/run/asterisk.ctl exist?) message while trying to connect to the Asterisk CLI, try to disable SELinux. In CentOS, this is done by changing the value of the SELINUX and SELINUXTYPE lines to disabled in /etc/selinux/config and rebooting your system:
# This file controls the state of SELinux on the system. # SELINUX= can take one of these three values: # enforcing - SELinux security policy is enforced. # permissive - SELinux prints warnings instead of enforcing. # disabled - No SELinux policy is loaded. SELINUX=disabled # SELINUXTYPE= can take one of three two values: # targeted - Targeted processes are protected, # minimum - Modification of targeted policy. Only selected processes are protected. # mls - Multi Level Security protection. SELINUXTYPE=disabled
Once inside the Asterisk CLI, run the following command:
geek-university*CLI> sip reload Reloading SIP == Parsing '/etc/asterisk/sip.conf': Found
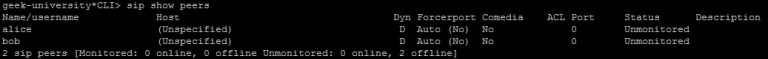
Now you can verify that the new SIP channels have been loaded using the sip show peers command:
As you can see from the last line of the output above, our peers are still offline. So let’s register a couple of devices to our Asterisk system.