There are three vCenter SSO policies that you can edit to conform to your company’s security standards:
1. Password policy – a set of rules and restrictions on the format and lifespan of user passwords. Note that this policy applies only to users in the vCenter Single Sign-On domain (vsphere.local).
To edit the password policy parameters, log in to your vCenter Server with a user that has vCenter Single Sign-On administrator privileges and go to Administration > Single Sign-On > Configuration:
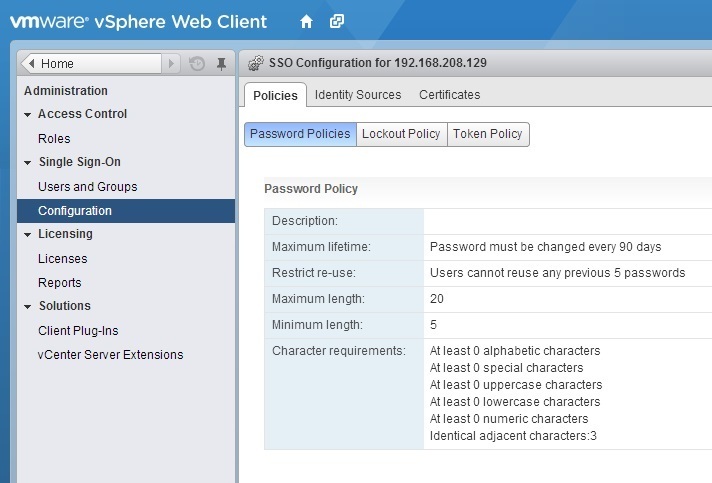
Under the Policies tab you can see the current password policies. For example, you can see that vCenter Single Sign-On passwords are set to expire after 90 days. Click the Edit button on the right to edit the password policy parameters:
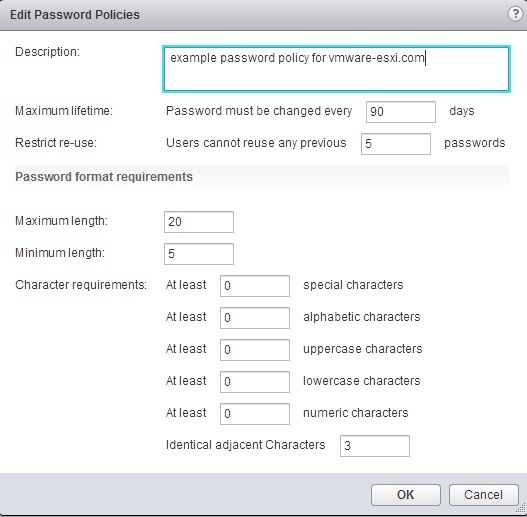
You can configure the following parameters:
|
Description
|
Password policy description. Required.
|
|
Maximum lifetime
|
Maximum number of days that a password can exist before it has to be changed.
|
|
Restrict re-use
|
Number of the user’s previous passwords that cannot be set again.
|
|
Maximum length
|
Maximum number of characters that are allowed in the password.
|
|
Minimum length
|
Minimum number of characters required in the password.
|
|
Character requirements
|
Minimum number of different character types required in the password.
|
|
Identical adjacent characters
|
Maximum number of identical adjacent characters allowed in the password.
|
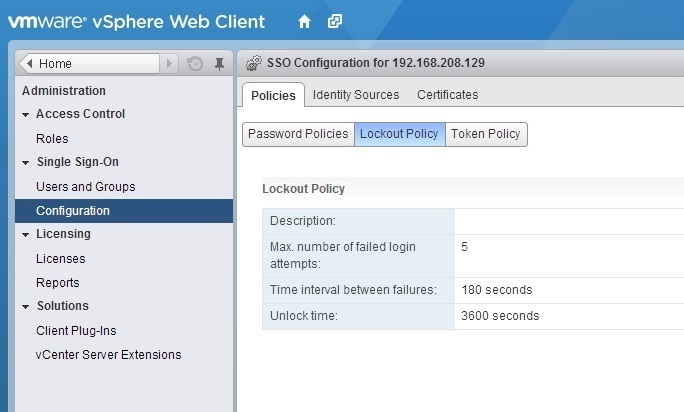
2. Lockout policy – specifies the condition under which a vCenter SSO account is locked when the user attempts to log in with incorrect credentials. Five login attempts and three minutes between failures are set by default. This policy also specifies the time that must elapse before the account is automatically unlocked.
To display the lockout policy parameters, click on the Policies tab and select Lockout Policy:
Click the Edit button on the right to edit the lockout policy parameters:
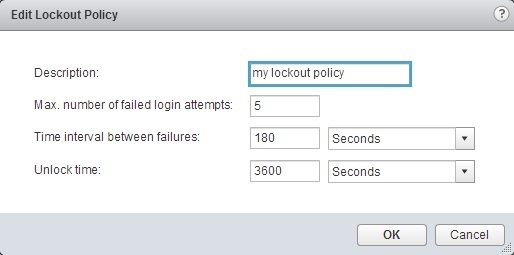
The following parameters can be configured:
|
Description
|
Description of the lockout policy. Required.
|
|
Max. number of failed login attempts
|
Maximum number of failed login attempts that are allowed before the account is locked.
|
|
Time interval between failures (seconds)
|
Time period in which failed login attempts must occur to trigger a lockout.
|
|
Unlock time (seconds)
|
Amount of time that the account remains locked. If you enter 0, the account must be explicitly unlocked by an administrator.
|
3. Token policy – specifies the clock tolerance, renewal count, token delegation count, and other token properties.
To see the lockout policy parameters, click on the Policies tab and select Token Policy:
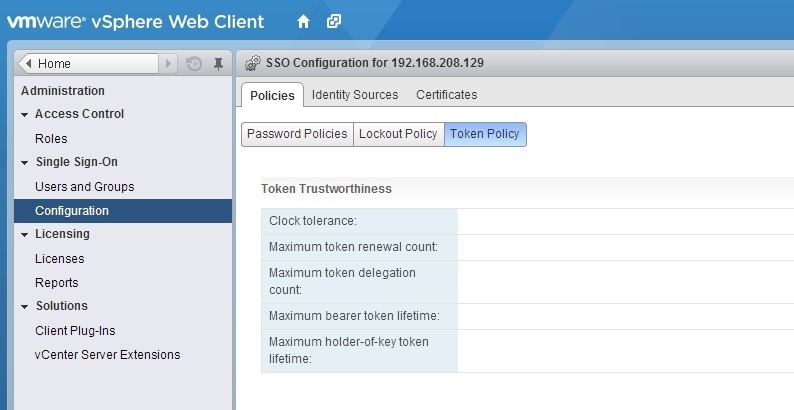
Click the Edit button on the right to edit the token policy parameters:
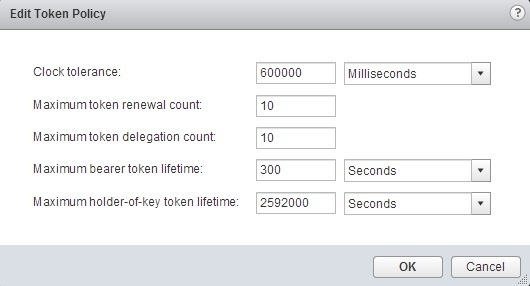
The following parameters can be configured:
|
Clock tolerance
|
Time difference, in milliseconds, that vCenter Single Sign-On tolerates between a client clock and the domain controller clock. If the time difference is greater than the specified value, vCenter Single Sign-On declares the token invalid.
|
|
Maximum token renewal count
|
Maximum number of times that a token can be renewed. After the maximum number of renewal attempts, a new security token is required.
|
|
Maximum token delegation count
|
Holder-of-key tokens can be delegated to services in the vSphere environment. A service that uses a delegated token performs the service on behalf of the principal that provided the token. A token request specifies a DelegateTo identity. The DelegateTo value can either be a solution token or a reference to a solution token. This value specifies how many times a single holder-of-key token can be delegated.
|
|
Maximum bearer token lifetime
|
Bearer tokens provide authentication based only on possession of the token. Bearer tokens are intended for short-term, single-operation use. A bearer token does not verify the identity of the user or entity that is sending the request. This value specifies the lifetime value of a bearer token before the token has to be reissued.
|
|
Maximum holder-of-key token lifetime
|
Holder-of-key tokens provide authentication based on security artifacts that are embedded in the token. Holder-of-key tokens can be used for delegation. A client can obtain a holder-of-key token and delegate that token to another entity. The token contains the claims to identify the originator and the delegate. In the vSphere environment, a vCenter Server obtains delegated tokens on a user’s behalf and uses those tokens to perform operations.
This value determines the lifetime of a holder-of-key token before the token is marked invalid.
|









