ASA security levels explained
ASA uses a security level associated with each interface. It is a number between 0 to 100 that defines the trustworthiness of the network that the interface is connected to; the bigger the number, the more trust you have in the network. For example, the most secure network, such as the inside LAN, should have the security level of 100. The outside network connected to an untrusted network (such as the Internet) should have the level of 0. The interface connected to the DMZ should have the security level set to somewhere between 1 and 99 (usually 50).
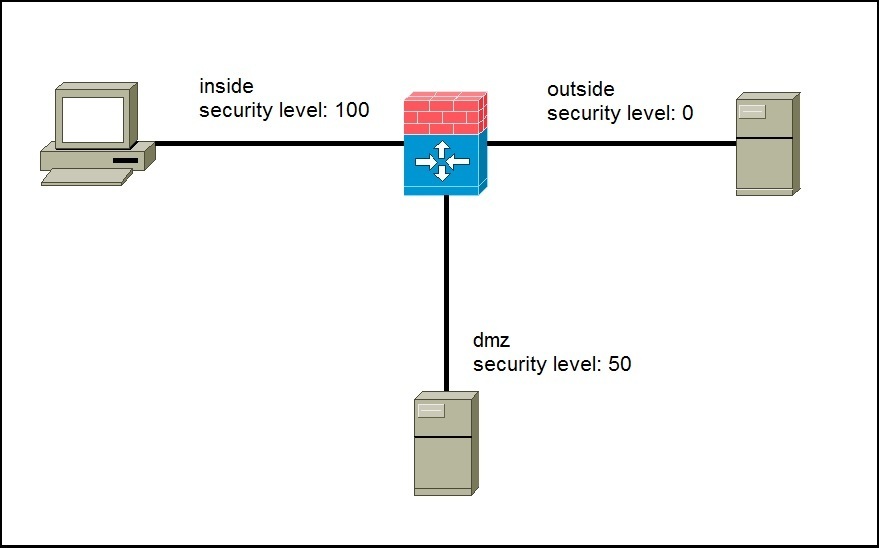
Security levels are used to define how traffic initiated from one interface is allowed to return from another interface. By default, the higher level security interfaces can initiate traffic to a lower level. The stateful inspection determines whether the reply traffic is allowed to make it back through. The following picture illustrates the concept:
In the picture above we have an example ASA network with three security levels defined:
- level 100 for the inside network
- level 50 for the DMZ network
- level 0 for the outside network
By default, ASA will stop all initial traffic that is trying to go from lower security levels to higher security levels. This means that, for example, a server on the outside network will not be able to start a converation with the server in our DMZ network or with the host in the inside network. The server in DMZ can initialize traffic out to the outside (from high to low, 50 to 0), but it can not initialize a conversation to the inside (from low to high, 50 trying to go to 100). The host on the inside can initiate traffic to both the DMZ and Internet server. When the server on the outside replies back to the inside host, the ASA will dynamically allow that return traffic.