Secure Shell (SSH) protocol
Just like Telnet, the Secure Shell (SSH) protocol enables a user to access a remote device and manage it. The key difference between Telnet and SSH is that SSH uses encryption. All data transmitted over a network (including usernames and passwords) is encrypted and secure from eavesdropping. SSH employs public key cryptography for the encryption.
A user on a client machine can use a software (an SSH client) to establish a connection to an SSH server running on a remote machine. Once the connection has been established, the user can execute commands on the remote device. Consider the following example:
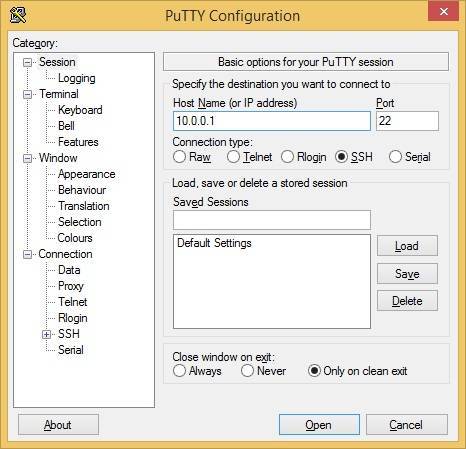
The network administrator wants to use his computer (Host A) to access and manage the router with the IP address of 10.0.0.1. The administrator will start an SSH client program on Host A and enter the IP address of the router R1 to access it (in this case, the client program is Putty):
The devices will agree upon the symmetric key that will be used for encryption and the administrator will be presented with the usual login screen.