Standard ACLs
Standard access control lists (ACLs) allow you to evaluate only the source IP address of a packet. Standard ACLs are not as powerful as extended access lists and can’t distinguish between the types of IP traffic, but they are less CPU intensive for the device.
Before configuring standard ACLs, here are a few things to have in mind when working with ACLs (both standard and extended):
- ACLs can contain multiple statements. The packet is always compared with each line of the access list in sequential order – it starts with the first line of the access list, move on to line 2, then line 3, etc.
- The packet is compared with lines of the access list only until a match is made. Once the condition is met, the packet is acted upon and no further comparisons take place.
- There is an implicit deny all at the end of each access list. This means that if a packet doesn’t match the condition on any of the lines in the access list, the packet will be discarded.
ACLs need to be applied to an interface on the device where you want the traffic filtered. You must also specify which direction of traffic you want the access list applied to. Two directions are available:
- inbound – ACL is applied to the traffic coming into the interface.
- outbound – the ACL is applied to the traffic leaving the interface.
To create a standard access list, the following command is used in the router’s global configuration mode:
R1(config)# access-list ACL_NUMBER permit|deny IP_ADDRESS WILDCARD_MASK
You can also use the host keyword to specify the host you want to permit or deny:
R1(config)# access-list ACL_NUMBER permit|deny host IP_ADDRESS
Once the access list is created, it needs to be applied to an interface. You do that by using the ip access-group ACL_NUMBER in|out interface subcommand. The in keyword specifies that the ACL will be applied to the the traffic coming into the interface, while the out keyword specifies that the ACL will be applied to the traffic leaving the interface.
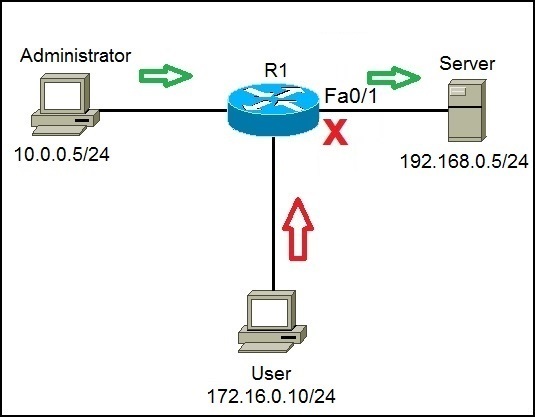
Let’s now configure standard ACLs. Consider the following network topology:
Server (192.168.0.5/24) holds some important documents that need to be available only to the administrator (10.0.0.5/24). We can configure an access list on R1 to enable access to Server only for the administrator’s workstation. Any other traffic going to Server should be blocked.
First, we need to allow traffic from the administrator’s workstation to the Server. We can use the following command on R1:
The command above permits traffic from the administrator’s IP addresses (10.0.0.5).
We will deny access to the user with the IP address of 172.16.0.10 using the following command:
Next, we need to apply the access list to an interface. It is recommended to place the standard access lists as close to the destination as possible. In our case, this is the Fa0/1 interface on R1. Since we want to evaluate all packets trying to exit out Fa0/1, we will specify the outbound direction:
The command above will force the router to evaluate all packets trying to exit out Fa0/1. If the administrator tries to access Server, the traffic will be allowed, because of the first statement (access-list 1 permit 10.0.0.5 0.0.0.0). However, if User tries to access Server, the traffic will be forbidden because of the second ACL statement (access-list 1 deny 172.16.0.10 0.0.0.0). Remember, the standard ACLs evalute only the source IP address of a packet.